7.1 Describe Azure directory services
Microsoft Entra ID is a directory service that enables you to sign in and access both Microsoft cloud applications and cloud applications that you develop.
Microsoft Entra ID also helps you maintain your on-premises Active Directory deployment.
For on-premises environments, Active Directory running on Windows Server provides an identity and access management service that's managed by your organization.
Microsoft Entra ID is Microsoft's cloud-based identity and access management service.
With Microsoft Entra ID, you control the identity accounts, but Microsoft ensures that the service is available globally.
When you secure identities on-premises with Active Directory, Microsoft doesn't monitor sign-in attempts, but if you connect Microsoft Entra ID, Microsoft monitors sign-in attemps, e.g. from unexpected location or unknown device.
Who uses Microsoft Entra ID?
- IT admins: admins use Microsoft Entra ID to control access to applications and resources
- App developers: Developers use Microsoft Entra ID to provide a standards-based approach for adding functionality to applications that they build, such as adding SSO functionality to an app or enabling an app to work with a user's existing credentials.
- Users: can manage their identities and take maintenance actions like self-service password reset.
- Online service subscribers: Microsoft 365, etc subscribers already use Microsft Entra ID to authenticate to their account
What does Microsoft Entra ID do?
- Authentication: verifying identity to access applications and resources
- Single sign-on: SSO enables you to remember only one username and one password to access multiple locations.
- Application management: Manage your cloud and on-premises apps by using Microsoft Entra ID. (계정 하나만)
- Device management: Microsoft Entra ID supports the registration of devices, which enables management of devices such as access policy to known devices.
Connecting on-premises AD with Microsoft Entra ID?
You can connect Active Directory with Microsoft Entra ID, enabling a consistent identity experience between cloud and on-premises using Microsoft Entra Connect.
Microsoft Entra Connect synchronizes changes between both identity systems, so you can use features like SSO, multifactor authentication, and self-service password reset under both systems.
Microsoft Entra Domain Services
Microsoft Entra Domain Services is a service that provides managed domain services such as domain join, group policy, lightweight directory access protocol (LDAP), and authentication.
Just like Microsoft Entra ID lets you use directory services without having to maintain the infrastructure supporting it, with Microsoft Entra Domain Services, you get the benefit of domain services without having to deploy, manage and patch.
Microsoft Entra Domain Services managed domain lets you run legacy applications in the cloud that can't use modern authentication methods, or where you don't want directory lookups to always go back to an on-premises AD DS environment.
Microsoft Entra Domain Services integrates with your existing Microsoft Entra tenant.
This integration lets users sign into services and applications connected to the managed domain using their existing credentials.
You can also use existing groups and user accounts to secure access to resources.
How does Microsoft Entra Domain Services work?
When you create a Microsoft Entra Domain Services managed domain, you define a unique nameset (domain name).
Two Windows Server domain controllers are then deployed into your selected Azure region (two DCs: replica set).
You don't need to manage, configure, or update these DCs, as it's done by Azure platform, including backups and encryption.
Is information synchronized?
A managed domain is configured to perform a one-way synchronization from Microsoft Entra ID to Microsoft Entra Domain Services.
You can create resources directly in the managed domain, but they aren't synchronized back to Microsoft Entra ID.
In a hybrid environment with an on-premises AD DS environment, Microsoft Entra Connect synchronizes identity information with Microsoft Entra ID, which is then synchronized to the managed domain.

7.2 Describe Azure authentication methods
Authentication is the process of establishing the identity of a person, service or device.
Azure supports multiple authentications methods, including standard passwords, single sign-on (SSO), multifactor authentication (MFA), and passwordless.

Single Sign-On (SSO)
Single sign-on (SSO) enables a user to sign in one time and use that credential to access multiple resources and applications from different providers.
For SSO to work, the different applications and providers must trust the initial authenticator.
More identities mean more passwords to remember and change → more complex for the users.
With SSO, you need to remember only one ID and one password.
Access across applications is granted to a single identity that's tied to the user, which simplifies the security model.
SSO is only as secure as the initial authenticator because the subsequent connections are all based on the security of the initial authenticator.
Multifactor authentication (MFA)
Multifactor authentication is the process of prompting a user for an extra form of identification during the sign-in process.
MFA helps protect against a password compromise in situations where the password was compromised but the second factor wasn't.
Multifactor authentication provides additional security for your identities by requiring two or more elements to fully authenticate.
MFA increases identity security by limiting the impact of credential exposure (e.g. stolen username and passwords).
With MFA enabled, an attacker who has a user's password would also need to have possession of the phone or fingerprint to fully authenticate → better security
Passwordless authentication
Passwordless authentication is more convenient because the password is removed and replaced with something you have, something you are or something you know.
Passwordless authentication needs to be set up on a device before it can work.
E.g. your computer is something you have and once it's been registered or enrolled, Azure now knows that it's associated with you. Now the computer is known, once you provide something you are (fingerprint), you can be authenticated without needing a password.
Three passwordless authentication options that integrate with Microsoft Entra ID:
- Windows Hello for Business: ideal for workers that have personal Windows PC: the biometric and PIN credentials directly tied to the PC, which prevents access from anyone else.
- Microsoft Authenticator App: Can also provide passwordless option
- FIDO2 security keys
7.3 Describe Azure external identities
An external identity is a person, device, service etc that is outside your organization.
Microsoft Entra External ID provides ways to securely interact with users outside of your organization.
With External Identities, external users can bring their own identities and to sign in.
The external user's identity provider manages their identity, adn you manage access to your apps with Microsoft Entra ID or Azure AD B2C to keep your resources protected.
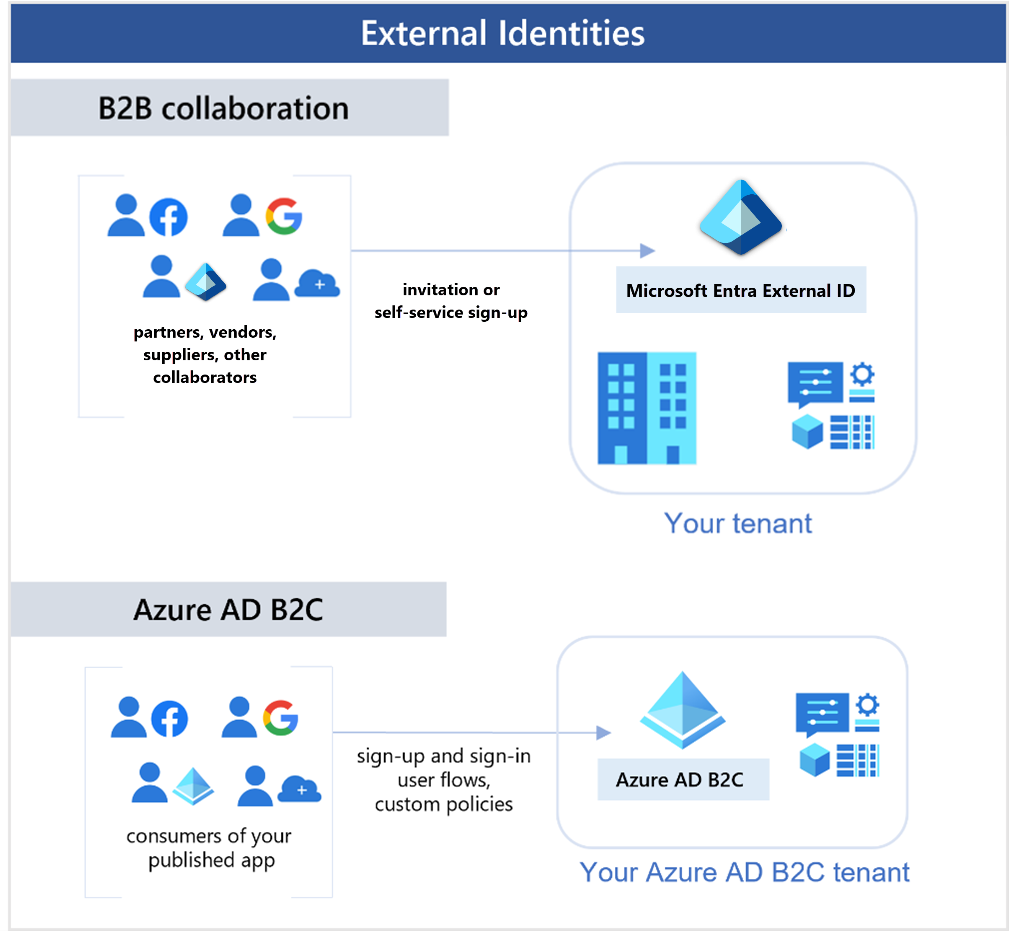
Capabilities that make up External Identities:
- Business to business (B2B) collaboration: Collaborate with external users by letting them use their preferred identity to sign-in to your Microsoft applications or other enterprise applications.
- B2B direct connect: Establish a mutual, two way trust with another Microsoft Entra organization for seamless collaboration. B2B direct connect currently supports Teams shared channels, enabling external users to access your resources from within their home instances of Teams.
- Microsoft Azure Active Directory business to customer (B2C): Publish modern SaaS apps or custom-developed apps to consumers and customers, while using Azure AD B2C for identity and access management.
7.4 Describe Azure conditional access
Conditional Access is a tool that Microsoft Entra ID uses to allow (or deny) access to resources based on identity signals.
These signals include who the user is, where the user is, and what device the user is requesting access from.
Conditional Access also provides a more granular MFA experience for users, e.g. a user might not have to do MFA if they are in a known location.
During sign-in, Conditional Access collects signals from the user, makes decisions based on those signals, and then enforces that decision by allowing or denying the access request or challenging for a MFA response.

Here, the signal might be the user's location, the user's device, or the application that the user is trying to access.
Based on these signals, the decision might be to allow full access if the user is signing in from their usual location.
If the user is signing in from an unusual location or a location that's marked as high risk, then access might be blocked entirely or possibly granted after the user provides a second form of authentication.
Enforcement is the action that carries out the decision.
For example, the action is to allow access or require the user to provide a second form of authentication.
When can I use Conditional Access?
Conditional Access is useful when you need to:
- Require MFA to access an application depending on the requester's role, location, or network.
- Require access to services only through approved client applications.
- Require users to access your application only from managed devices.
- Block access from untrusted sources, such as access from unknown or unexpected locations.
7.5 Describe Azure role-based access control
The principle of least priviledge says you should only grant access up to the level needed to complete a task.
If you only need read access to a storage blob, then you should only be granted read access to that storage blob.
Write access to that blob shouldn't be granted, nor should read access to other storage blobs.
Azure enables you to control access through Azure role-based access control (Azure RBAC).
Azure provides built-in and customized roles that describe access rules for cloud resources.
How is role-based access control applied to resources?
Role-based access control is applied to a scope, which is a resource or set of resources that this access applies to.

A management group, subscription, or resource group might be given the role of owner, so they have increased control and authority.
An observer (don't make updates) can be given a role of Reader ofr the same scope, enabling them to review or observe the management group, subscription, or resource group.
Scopes include:
- A management group (collection of multiple subscripions)
- A single subscriptin
- A resource group
- A single resource
Azure RBAC is hierarchical, so when you grant access at a parent scope, those permissions are inherited by all child scopes.
Examples:
- when you assign the owner role to a user at the management group scope, that user can manage everything in all subscriptions within the management group
- when you assign the reader role to a group at the subscription scope, the members of that group can view every resource group and resource within the subscription.
How is Azure RBAC enforced?
Azure RBAC is enforced on any action that's initiated against an Azure resource that passes through Azure Resource Manager.
Resource Manager is a management service that provides a way to organize and secure your cloud resources.
7.6 Describe Zero Trust model
Zero Trust is a security model that assumes the worst case scenario and protects resources with that expectation.
Zero Trust assumes breach at the outset, and then verifies each request as though it originated from an uncontrolled network.
Organizations need a security model that effectively adapts to the complexity of the modern environment; embraces the mobile workforce; and protects people, devices, applications, and data wherever they're located.
Zero Trust security model is based on these guiding primciples:
- Verify explicitly: Always authenticate and authorize based on all available data points
- Use least priviledge access: Limit user access
- Assume breach: Minimize blast radius and segment access. Verify end-to-end encryption. Use analytics to get visibility, drive threat detection and improve defenses.
Adjusting to Zero Trust
Traditionally, corporate networks were restricted, protected, and generally assumed safe.
Only managed computers could join the network, VPN access was tightly controlled, and personal devices were frequently restricted or blocked.
In Zero Trust model, instead of assuming that a device is safe because it's within the corporate network, it requires everyone to authenticate.
Then grants access based on authentication rather than location,

7.7 Describe defense-in-depth
The objective of defense-in-depth is to protect information and prevent it from being stolen by those who aren't authorized to access it.
A defense-in-depth strategy uses a series of mechanisms to slow the advance of an attack that aims at acquiring unauthorized access to data.
Layers of defense-in-depth
Defense-in-depth: data to be secured at the center and all the other layres functioning to protect that central data layer.

Each layer provides protection so that if one layer is breached, a subsequent layer is already in place to prevent further exposure.
This approach removes reliance on any single layer of protection and slows down an attack and provides alert information that security teams can act upon.
Role of each layer:
- Physical security layer:
First line of defense to protect computing hardware in the datacenter. Physically securing access to buildings and controlling access to computing hardware within the datacenter.
- Identity and access layer:
Controls access to infrastructure and change control. The identity and access layer is all about ensuring that identities are secure, that access is granted only to what's needed and that sign-in events and changes are logged. It's important to: control access to infrastructure and change control; use SSO and MFA; and audit events and changes.
- Perimeter layer:
Protects from network-based attacks against your resources. Important to: use DDoS protection to filter large-scale attacks before can cause denial of service for users; and user filrewalls to identify and alert on malicious attacks against the network.
- Network layer:
Focus is on limiting the network connectivity across all your resources to allow only what's required. By limiting this communication, you reduce the risk of an attack spreading to other systems in the network.
- Compute layer:
Malware, unpatched systems and improperly secured systems open your environments to attacks. Important to: secure access to VMs and implement protetion to keep systems patched.
- Application layer:
Helps ensure that applications are secure and free of security vulnerabilities by storing sensitive application secrets in a secure storage medium.
- Data layer:
Controls access to business and customer data
7.8 Describe Microsoft Defender for Cloud
Defender for Cloud is a monitoring tool integrated to Azure for security posture management and threat protection.
It monitors your cloud, on-premises, hybrid, and multicloud environments to provide guidance and notifications aimed at strengthening your security posture.
Protection everywhere you're deployed
Because Defender for Cloud is an Azure-native service, many Azure services are monitored and protected without needing any deployment.
For on-premises datacenter or another cloud environment, Defender for Cloud can automatically deploy a Log Analytics agent to gather security-related data.
Defender for Cloud helps across:
- Azure PaaS ervices
- Azure data services
- Networks
Defend your hybrid resources
You can also add Defender for Cloud capabilities to your hybrid cloud environment to protect your non-Azure servers.
Access, Secure, and Defend

Defender for Cloud fills three vital needs:
- Continuously Assess:
Defender for Cloud helps you continuously assess your environment, and you will have regular, detailed vulnerability scans that cover your compute, data and infrastructure.
- Secure:
From authentication methods to access control to the concept of Zero Trust, security in the cloud is essential.
To be secure in the cloud, workloads need to be secure and to do it, you need security policies in place that are tailored to your environment.
In Defender for Cloud, you can set your policies to run on management groups, across subscriptions and even for a whole tenant.
- Defend:
The first two areas were focuses on assessing, monitoring and maintaining the environment.
Defender for Cloud also provides security alerts and advanced threat protection features.
7.9 Module Assessment
1. Which Microsoft Entra tool can vary the credentials needed to log in based on signals, such aswhere the user is located?
Conditional Access
2. Which security model assumes the worst-case security scenario, and protects resources accordingly?
Zero Trust
3. A user is simultaneously assigned multiple roles that use role-based access control. What are their actual permissions? The role permissions are: Role 1 - read || Role 2 - write || Role 3 - read and write.
Read and write




댓글