목차
What is security?
Computer security deals with protecting data, programs, and systems against intelligent adversaries.
Safety vs Security:
- Safety means being secure against unintended threats
- Security is the protection against deliberate threats.
Why is security hard?
Security is hard to test for.
Building secure applications requires deep understanding of all technologies involved in the design and implementation of the system.
One vulnerability can cripple the system (하나의 취약점이 시스템 전체를 무너뜨릴 수 있다)
Not all dependencies are known
It is not all technical, users play a role too.
Security principles: CIA triad
Systems must be available to users, users should be able to trust (verify) that the data is correct, and data should not be accessed by unauthorized persons.
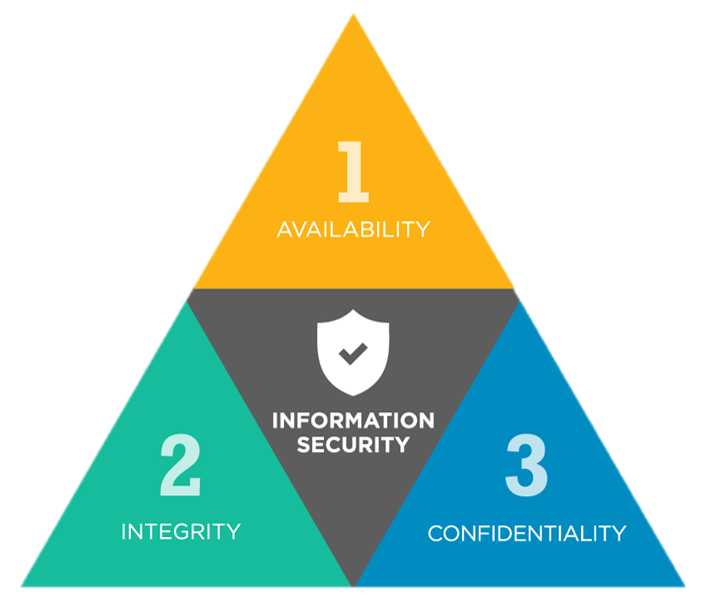
- Confidentiality (비밀성, 기밀성)
허가되지 않은 자가 정보를 보지 못하도록 방지하는 것
- Integrity (무결성)
허가되지 않은 자가 정보를 변경할 수 없도록 하는 것.
- Availability (가용성)
허가된 자가 정보에 접근하려 할 때 방해가 없도록 하는 것. (악인들이 정보에 접근하는 것을 방지하고 적절하게 허가된 자만 접근할 수 있도록 하는 것)
Tools for Confidentiality
Encryption
Ensure that data cannot be read when someone gets their hands on it
Access control systems
Make it hard to get the data when the user is unauthorized.
Policies and governance
Mandate secure data practices
Tools for Integrity
Data validation
Validate data at various stages to ensure that it is still intact (e.g. Digital signatures, error detection)
Change management and version control
Control and document changes to data to ensure transparency and accountability
Tools for Availability
Redundancy and failover
Design systems with backup mechanisms to mitigate single points of failure
Load balancing
Distribute traffic across various resources
Monitoring and alerting
Monitor for early signs of problems to identify system failures before they become a large issue.
Computer security threat
Threats are potential violations of security posed by attackers (attackers have different profiles and motives)
When evaluating the security of a program or website, it's essential to consider the context (potential attacker, ...)
Computer security is context-dependent and revolves around a specific attacker or threat model.
There is no universal solution that can defend against all types of threats.
No One-Size-Fits-All
Recognize that security measures should be tailored to specific threats and scenarios
Continuous Evaluation
Regularly assess and update security measures based on evolving threat landscapes.
Layered Defense
Implement a multi-layered security approach to address different levels of threats.
Threat Model
A threat model serves as a strategic framework that identifies potential attacks and adversaries a system aims to safeguard against.
Threat models help in understanding and preparing for various security risks.

Types of threat actors
Threat actors have varying capabilities.
A hacking group backed by a nation has access to much more resources than someone hacking on their own.
Threat actors have varied motivations, ranging from financial gain to political or ideological reasons.

Coordinated Vulnerability Disclosure
CVD is an ethical practice where security researchers or individuals who discover vulnerabilities in a system responsibly report them to the affected organization.
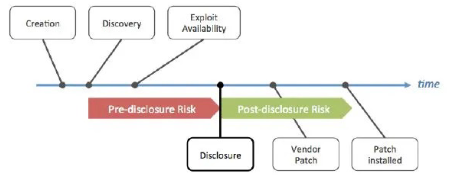
Bug bounty program
Organizations offer rewards to ethical hackers (bug hunters) for responsibly discovering and reporting security vulnerabilities.
Bug bounty programs incentivize ethical hacking to improve cybersecurity.
Patch adoption is slow
Organizations need some time before their systems are patched, and often this takes a very long or is not done at all.
Because patching is slow, there is a window where organizations are vulnerable even after exploits are readily available.
Eggshell defense
Eggshell defense: practice of protecting a network or system by assuming that it's vulnerable and treating it as such, even if the specific vulnerabilities aren't immediately apparent.
취약하다고 가정하고 네트워크나 시스템 보호를 미리 하는 거
Attackers only have to succeed once, defenders have to succeed every time

Cyber Kill Chain
Paradigm shift in cyber security, balancing the playing field: Attackers only have to be detected once.
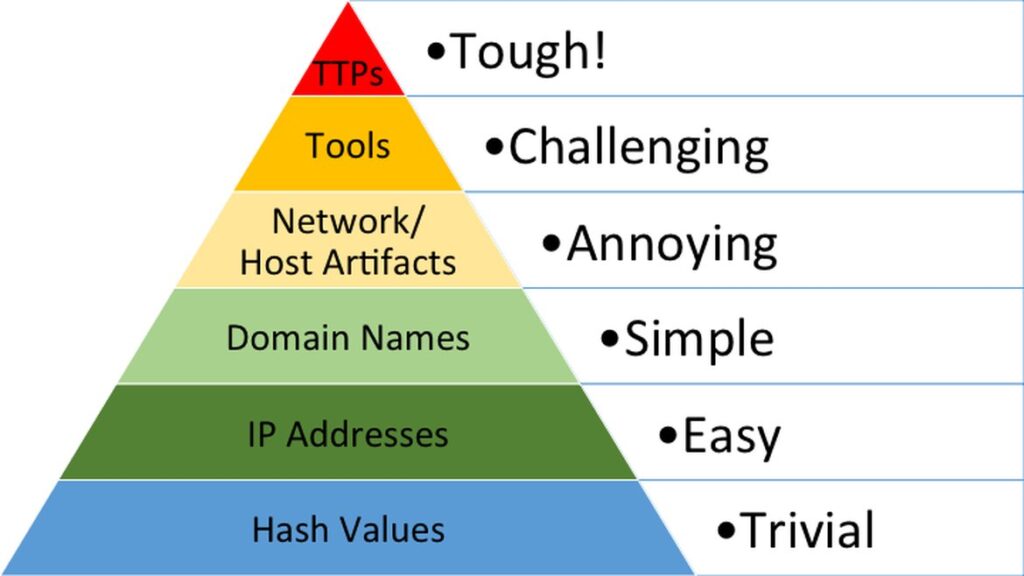
Pyramid of pain
We can detect cyber attacks on multiple levels.
The higher the level of detection, the harder it becomes for attackers to circumvent the measure.
즉, 탐지 레벨이 올라갈수록, 공격자가 피해 가기 어렵다.
Security by design
Security by design is an approach that integrates cybersecurity measures into the design and development processes of systems and applications from the outset.
Identifying and addressing security risks early in the development process leads to a more secure product.
Integrating security from the beginning is more cost-effective than retroffiting security measures later.
Regulatory requirements make it mandatory to think about security in an early stage.
Defense in Depth
Defense in Depth is a cybersecurity strategy that involves deploying multiple layers of security controls to protect against various types of threats.
This reduces the risk of a single security control failure compromising the entire system.
Usable security
Usable security is an approach that seeks to integrate effective cybersecurity measures while maintaining a positive and user-friendly experience.
Even for the best security measure, if it is not usable, people will work around them, which creates even more security risks.
이건 usability와 security의 균형을 찾는 것. 보안만 생각해서 시스템을 사용하기 어렵게 만들면 안 된다.
'학교 > CS' 카테고리의 다른 글
| Lecture 6: OS - Level Security (0) | 2024.03.03 |
|---|---|
| Lecture 5: Internet security (0) | 2024.03.03 |
| Lecture 4: Firewalls and Intrusion detection (0) | 2024.03.03 |
| Lecture 3: Denial of Service and Botnets (0) | 2024.03.03 |
| Lecture 2: Network Security Physical Layer (0) | 2024.03.03 |




댓글