목차
Attacks on Availability in the OSI Model
Availability can be attacked on every layer ofthe model.
The best-known attack is a DDoS attack, overwhelming a system with a lot of traffic.
Background - Network layer
IP datagrams can be exchanged between any two nodes (provided they both have an IP address)

The server determines who sent the packet based on the Source IP.
IP 스푸핑이란 IP (Internet Protocol) 자체의 보안 취약성을 악용한 것으로 자신의 IP 주소를 속여서 접속하는 공격을 말한다. 신뢰 관계에 있는 두 시스템 사이에서 허가받지 않은 자가 자신의 IP 주소를 신뢰 관계에 있는 호스트의 IP 주소로 바꾸어 속이는 것으로 공격자가 마치 신뢰성 있는 자가 송신한 것처럼 패킷의 소스 IP 주소를 변조하여 접속을 시도하는 침입 형태를 말한다.

Background - Transport layer
TCP is a connection-based protocol which needs a "handshake" to initialize a connection.

TCP Handshake:
The client sends a SYN (synchronize) packet to the server, indicating its intention to establish a connection.
The server responds with a SYN-ACK (synchronize acknowledge) packet, acknowledging the client's request and indicating its readiness to establish a connection.
Finally, the client sends an ACK (acknowledge) packet to confirm the connection establishment.
UDP is a connectionless protocol.

DoS attack
A Denial of Service (DoS) attack overwhelms a target system with a flood of traffic, rendering it unavailable to users.
Attackers aim ot disrupt services, causing financial losses or reputational damage.
서비스 거부(DoS) 공격은 악의적인 행위자가 장치의 정상적인 작동을 방해하여 컴퓨터 또는 기타 장치를 사용하려는 사용자가 해당 장치를 사용할 수 없게 만드는 것을 목표로 한다. DoS 공격은 일반적으로 정상적인 트래픽을 처리할 수 없을 때까지 대상 시스템을 요청으로 압도하거나 폭주시켜 추가 사용자에 대한 서비스 거부를 초래하는 방식으로 작동한다. DoS 공격은 단일 컴퓨터를 사용하여 공격을 시작하는 것이 특징이다.
DDoS - Cheap to perform, expensive to mitigate
Types of DoS attacks
Volumetric Attacks
Overwhelm victims with a high volume of traffic.
Application Layer Attacks
Target specific applications to exhaust resources.
Amplification attack
For attackers to overwhelm victims with a high volume of traffic, attackers use an intermediary server that returns a large response to a query to create an Amplification attack.
Requirements for this attack are:
- A server that provides large responses on small queries.
- The ability to spoof an IP address.
Amplification attack can be done with many protocols, commonly over UDP.
A popular protocol is DNS, where the attacker spoofs (도용) the IP address of a victim.
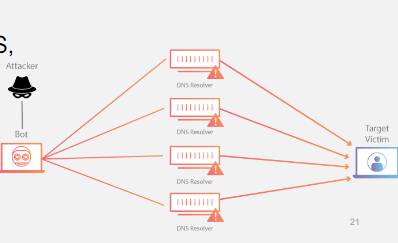
조금 더 구체적으로 설명하면 다음과 같다.
1. Spoofing the source IP: The attacker spoofs the source IP address (victim) in the requests sent to the vulnerable servers. By using the victim's IP address as the source, the attacker ensures that the responses from the servers are sent to the victim instead of the attacker.
2. Amplification: The attacker sends a small request to the server, and the server respnds with much larger responses. This amplification effect increases the volume of traffic directed towards the victim, making it more difficult for the victim's network infrastructure to handle the incoming requests.
Protocol Attacks
Exploit vulnerabilities in network protocols.
Instead of congesting the Internet line, attackers also target protocols to drain resources of a system to the point where the system no longer functions.
These attacks do not need as much bandwidth as volumetric attacks but do need some exploitable element in a protocol.
Targets the Network and Transport layer.
A common protocol attakc is the TCP SYN Flood.
일반 TCP Handshake

TCP SYN Flood를 하면:

설명:
1. In a TCP SYN flood attack, the attacker sends a large number of SYN packets to the targeted server, each with a spoofed source IP address. These SYN packets appear to be legitimate connection requests, but the source IP addresses are typically fake or unreachable.
2. Upon receiving the SYN packets, the targeted server allocates resources to establish a connection with each spoofed source IP address and sends back SYN-ACK packets. However, because the source IP addresses are spoofed, the server never receives the expected ACK packets to complete the three-way handshake. As a result, the server keeps these connections in a half-open state, consuming resources such as memory and processing power.
3. As the attacker continues to send SYN packets, the server's resources become overwhelmed with half-open connections. Eventually, the server runs out of resources to handle legitimate connection requests, leading to a denial of service for legitimate users trying to establish connections with the server.
Defenses - TCP SYN Cookies
Increasing the amount of "waiting" connections does not protect us.
We need to shift the burden away from our server.
즉, waiting conection을 처리할 수 있는 양을 늘려도 효과는 없다. 이 waiting connection들을 처리하는게 관건.
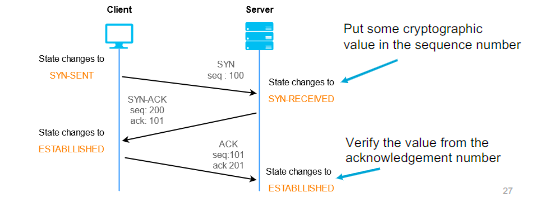
설명:
1. Initial Connection Request: When a client sends a SYN packet to initiate a TCP connection, the server generates a SYN cookie instead of allocating resources for a half-open connection. The SYN cookie includes information about the client's connection request, such as its source IP address and port number, as well as a cryptographic hash of this information.
2. SYN-ACK Response: Instead of responding with a SYN-ACK packet containing a sequence number and allocating resources for a half-open connection, the server includes the SYN cookie in the initial response. This response does not consume server-side resources beyond generating the SYN cookie.
3. Client Confirmation: When the client receives the SYN-ACK response containing the SYN cookie, it generates an ACK packet using the SYN cookie and sends it back to the server. This ACK packet confirms the client's intention to establish the connection and includes the same information used to generate the SYN cookie.
4. Connection Establishment: Upon receiving the ACK packet, the server verifies the authenticity of the SYN cookie by recalculating the cryptographic hash using the information from the ACK packet. If the verification is successful, the server establishes the connection as usual, allocating resources and allowing communication to proceed.
Measuring TCP SYN Floods
SYN-ACKs scatter over the Internet, being sent to random IP addresses.
If we have a lot of IP addresses, we can identify ongoing attacks.
This traffic is called backscatter.
즉, TCP Handshake에서 나온 SYN-ACKs 들은 랜덤 IP 주소들로 보내지는데 만약에 다수의 IP 주소를 보유하고 있으면 패턴이나 공격인지 아닌지를 파악할 수 있다.
Application Layer attacks
Application layer attacks specifically target the highest layer of the OSI model, focusing on the application and services provided to end-users.
The traffic generated by this attack is harder to identify as malicious traffic, as it closely resembles normal user traffic.
E.g. HTTP Flood
HTTP Flood
In a HTTP Flood, the attacker requests many pages, images, and/or other (large) files from a website at once.
As the attacker must complete the TC handshake to do this, the attack cannot be spoofed.
즉, 공격자가 다수의 용량이 큰 파일들을 사이트에서 요청한다. 이렇게 트래픽이 늘어나면 서버가 처리를 못 한다는 내용.

DDoS Mitigation
- Redundant network infrastructures ensure that a single point of failure cannot bring down the entire system.
- Traffic filtering aims to identify malicious packets and block them.
- Content Delivery Networks distribute and cache content over a large network, which can absorb and mitigate the DDoS traffic by serving content from distributed servers.
- Web Application Firewalls can protect against application layer attacks by identifying malicious traffic.
Botnet
A botnet is a network of compromised computers (bots) that are under the control of a single entity, usually a malicious actor.
Purpose: Botnets are typically used for various malicious activities, including distributed denial of service (DDoS) attacks, spreading malware, and stealing sensitive information.
Architecture of a botnet
- Infected devices (bots) - can be any device: IoT, PC, phones
- Command and control (C2 or C&C) infrastructure
→ the bots receive commands through the C2 infrastructure
- Communication channels: many protocols are used: IRC, HTTP, P2P, Blockchain
Architecture of a botnet - Mirai
Infects IoT devices
Propagates like a worm
C2 servers are centralized
Telnet-like communication channel
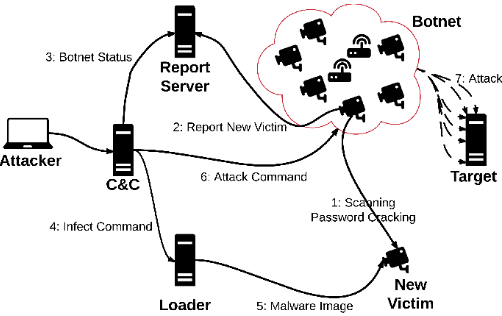
설명:
1. Botnet Controller (C&C Server):
The central component of the Mirai botnet is the Botnet Controller, also known as the Command and Control (C&C) server.
The C&C server is typically operated by the attackers and serves as the command center for controlling the infected IoT devices (bots).
The C&C server issues commands to the infected devices, instructing them to carry out various activities, such as launching DDoS attacks or scanning for vulnerable devices to infect.
2. Infected IoT Devices (bots):
Once infected, these devices become part of the Mirai botnet and are controlled by the C&C server.
Infected devices continuously communicate with the C&C server to receive commands and updates.
3. Scanning Module
Mirai includes a scanning module that enables infected devices to scan the Internet for other vulnerable IoT devices to infect.
The scanning module looks for devices with specific vulnerabilities, such as those with default usernames and passwords or known security flaws.
When vulnerable devices are found, the scanning module attempts to exploit the vulnerabilities to gain unauthorized access and infect them with the Mirai malware.
4. Propagation
Once an IoT device is infected with Mirai, it becomes part of the botnet and can be used to propagate the malware to other vulnerable devices.
The scanning module continuously searches for new devices to infect, rapidly expanding the size of the Mirai botnet.
Architecture of a botnet - Emotet
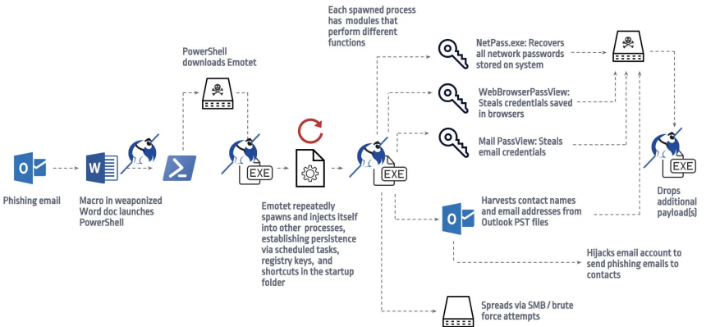
1. Propagation Mechanism:
Phishing email that contains malicious attachments or links
Once a user interacts with the malicious content, Emotet is downloaded and executed on the victim's system.
2. Command and Control (C&C) Infrastructure:
Emotet communicates with a network of command and control servers operated by the attackers.
These C&C servers serve as the central control point for managing infected devices and issuing commands to them.
Emotet-infected devices regularly communicate with the C&C servers to receive updates, download additional payloads, and exfiltrate stolen data.
3. Modular design:
Emotet has a modular architecture, allowing it to be highly adaptable and versatile in its malicious activities.
Emotet modules can include functionalities for spreading the malware to other devices, stealing sensitive information, conducting reconnaissance on infected systems, and performing other malicious activities.
4. Credential theft and Information Stealing:
Emotet is known for its ability to steal sensitive information, such as login credentials, email contacts, and financial data.
5. Payload Delivery
Emotet can act as a malware downloader, delivering additional payloads to infected devices.
These payloads can include ransomware, banking Trojans, information stealers, or other malware strains.
Mitigating botnets
- Securing many devices to make harder to compromise a large number of devices
- Taking down command and control infrastructure: the servers are often located in multiple countries and require collaboration between law-enforcement agencies
- Blocklisting devices that are infeced by a botnet so that owners clean them
Botnets constantly evolve to evade detection
Domain Generation Algorithm (DGA)
A static domain name or IP address can be blocked.
Malware authors generate many domain names and only have to register one.
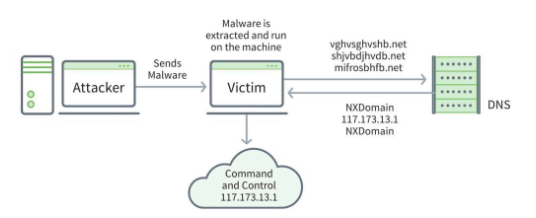
Peer to peer architecture
Command and Control servers might be taken down
Using the bots as C2 channel makes the botnet redundant (불필요한)
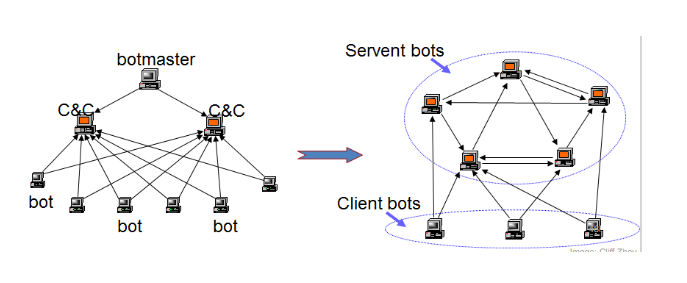
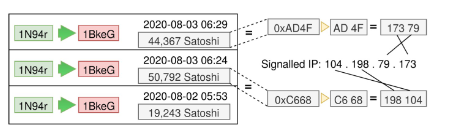
Sending the C2 location through the blockchain
Complete control over the C2 location, and changeable at any moment
Decentrialized by design, blockchain will not be taken down.
'학교 > CS' 카테고리의 다른 글
| Lecture 6: OS - Level Security (0) | 2024.03.03 |
|---|---|
| Lecture 5: Internet security (0) | 2024.03.03 |
| Lecture 4: Firewalls and Intrusion detection (0) | 2024.03.03 |
| Lecture 2: Network Security Physical Layer (0) | 2024.03.03 |
| Lecture 1: Introduction to Computer Security (0) | 2024.03.03 |




댓글