목차
Firewall
In Computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet.
Firewalls divide the untrusted outside of a network from the more trusted interior of a network.
The importance of firewalls
- It prevents (vulnerable) services to be accessed from outside the network.
- It segments networks.
- It reduces the attack surface (중요)

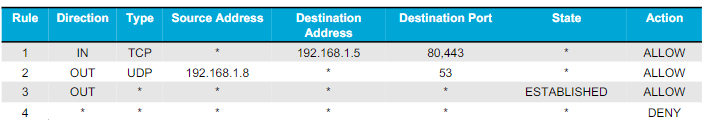
Firewall rules
The website at 192.168.1.5 should be reachable from the Internet.
The Internal DNS server at 192.168.1.8 should be able to reach other DNS servers.
Other connections should be denied.

Firewall in the network model
A firewall compares network traffic to a set of rules.
To match the rules to the traffic, it must process several packet layers to obtain the needed data.
For example: to allow the webserver to be reached, packets need to be processed up to the transport layer.
Types of firewalls
Firewalls can be implemented in Software or Hardware:
- Software - Slower, but easier to deploy on single machines
- Hardware - Faster, can be safer, but expensive
Firewalls can differ in the amount of Network Layers they process:
- Packet size (data link layer)
- MAC (data link layer) and IP (IP layer) filtering
- Port filtering (transport layer)
- Deep packet (application layer)
Four different firewalls:
- Packet filtering firewall
- Stateful inspection firewall
- Application-level gateway
- Circuit-level gateway
Packet filtering firewall
Packet filtering firewall compares packet header information to a set of rules.
Very fast - a minimal amount of processing is required.
Many rules are needed, making the firewall hard to maintain and prone to human error.
Allows access to services based on network data, does not allow for the blocking of specific application commands.
Stateful inspection firewall
Maintains state between packets, allowing for more complex rules.
Similar to packet filtering but remembers past events, allowing for rules that allow traffic from outside if the connection was started from inside the network.
Stateful inspection firewalls can be used to keep track of TCP sequence numbers and block connections that are acting suspicious.
Some stateful firewalls can inspect a limited amount of application-layer data for well-known protocols.
Keeping state is more expensive than simply packet filtering.
Application-level gateway
Also called application proxy.
Relays application layer data between user and application.
Can be used to block specific features of an application that you do nto want to be used.
Requires a lot of processing and does not scale well as it needs to be able to parse the application context.
Circuit-level gateway
Also called circuit-level proxy
Relays application layer data between user and application.
Does not parse the application layer contents, but determines which connections are allowed.
An example of such a firewall is a SOCKS proxy
SOCKS proxy
1. A user authenticates with the proxy
2. The user requests a specific IP and port
3. If the user is allowed to make that connection, the proxy sets up a connecion to the IP and port and relays the application-layer data.

Firewall use-case: TCP SYN scan
Attackers often scan a network to find vulnerable services.

To detect this, use a stateful firewall to block excessive scanning (and bruteforcing).
If attackers scan slow enough, they will still be able to scan the network.
Internet-wide scanning detection
People are scanning the entire Internet, so every IP address will see these scanning packets.
By looking at network traffic we can identify unsolicited packets.
If we monitor on many IP addresses, we get a good overview of who is scanning the Internet.
De-Militarized Zone (DMZ)
A DMZ is common in network architectures to allow some services to be reached from the Internet.
The Internal network is separated from the DMZ using a second firewall, which can be used for more stringent filtering.
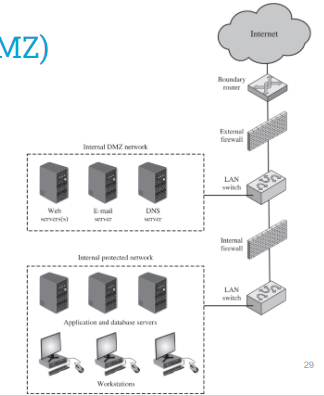
Different levels of security
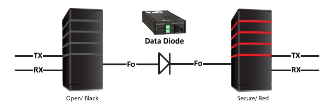
Physically separating infrastructure can be key to keep them safe.
High value systems are "air-gapped" and can only be accessed from specific terminals that are physically protected.
Data diodes can allow traffic to flow in, but no traffic to flow out.
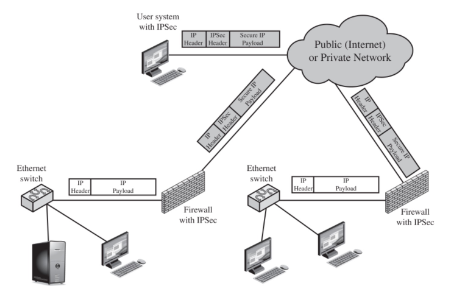
Virtual Private Network (VPN)
Accessing a (corporate) network from the outside is dangerous and therefore usually firewalled.
Sometimes it's required to link multiple facility networks over the Internet or provide employees with a way to work from multiple places securely.
A VPN can be used to encrypt data on lower layers to create a "transparent" tunnel that allows users to connect securely to a LAN network over the Internet.
IPSec is a protocol that adds an extra part to the Network layer, allowing to connect through a firewall onto a network.
It is usually cheaper than having private Internet cables.
Why intrusion detection matters
For someone who broke through the firewall
Firewalls aim to prevent attacks by reducing attack surface, but do not often detect attacks
You cannot block all traffic in a firewall
Attacks have multiple stages, all allowing for detection
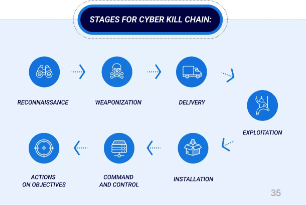
Intrusion Detection System (IDS)
An intrusion detection system is a device or software application that monitors a network or systems for malicous activity or policy violations.
Types of intrusion detection systems
An IDS can be either:
- Host-based (HIDS) - Monitors events on a host, such as system logs.
- Network-based (NIDS) - Monitors network data and can use deep-packet inspection to identify malicious activity.
IDS can have different types:
- Heuristic - Matches data to pre-defined rules
- Signature - Matches data to known indicators (e.g. flagged IP addresses)
- Anomaly - Determines what is normal data and identifies data that deviates from the norm.
Anomaly detection
Starts by gathering base-line data to consider as normal.
Classifies data using a variety of approaches:
- Statiscal - using various mathematical models
- Knowledge based - relying on expert knowledge to classify observed behavior
- Machine learning - automatically determine whether the observed data matches the baseline
Host-based IDS
Monitors activity on a system
A virus scanner is a type of HIDS
Common data sources for a HIDS include:
- System call traces
- Log files
- Integrity checksums
- Registry access patterns
Distributed HIDS
A distributed HIDS collects all data of various systems in the same place to create a more effective IDS
This requires devices in the network to run programs that collect telemetry and forward it to a central location.
There can be privacy concerns when collecting information about the systems of employees.
Network-based IDS
Monitors activity on a network.
Two types of sensors:
- Inline
- Passive
The location of the sensor matters a lot.
Sending traffic to a NIDS
Switches have SPAN ports that can be used to copy all data received on the switch.
If the switch receives more data than the SPAN port or the ethernet cable can handle, the data is not complete.
A wiretap on the raw network line will also provide a copy of the data and might be more complete.

Honeypots
A honeypot is a decoy system that is designed to lure potential attackers away from critical systems.
A honeypot has several goals:
- Divert attackers away from accessing real systems
- Collect information about the goals of an attacker
- Alert administrators of strange behavior
Honeypots are set up such that there is no reason to ever contact them, so if they are contacted, there is a high chance that it is malicious.
Location of sensors in a network
Sensors can be placed in many parts of the network:
- Behind the border firewall or at the level of the border firewall.
- In the DMZ
- In a specific part of the network, such as the network segment with employee devices.
The traffic collected is different at every point, depending on the threat profile of the organization.
'학교 > CS' 카테고리의 다른 글
| Lecture 6: OS - Level Security (0) | 2024.03.03 |
|---|---|
| Lecture 5: Internet security (0) | 2024.03.03 |
| Lecture 3: Denial of Service and Botnets (0) | 2024.03.03 |
| Lecture 2: Network Security Physical Layer (0) | 2024.03.03 |
| Lecture 1: Introduction to Computer Security (0) | 2024.03.03 |




댓글